生成密钥
keytool -genkey -alias java-lonely -keyalg RSA -keystore /Users/xietao/Downloads/java-lonely.keystore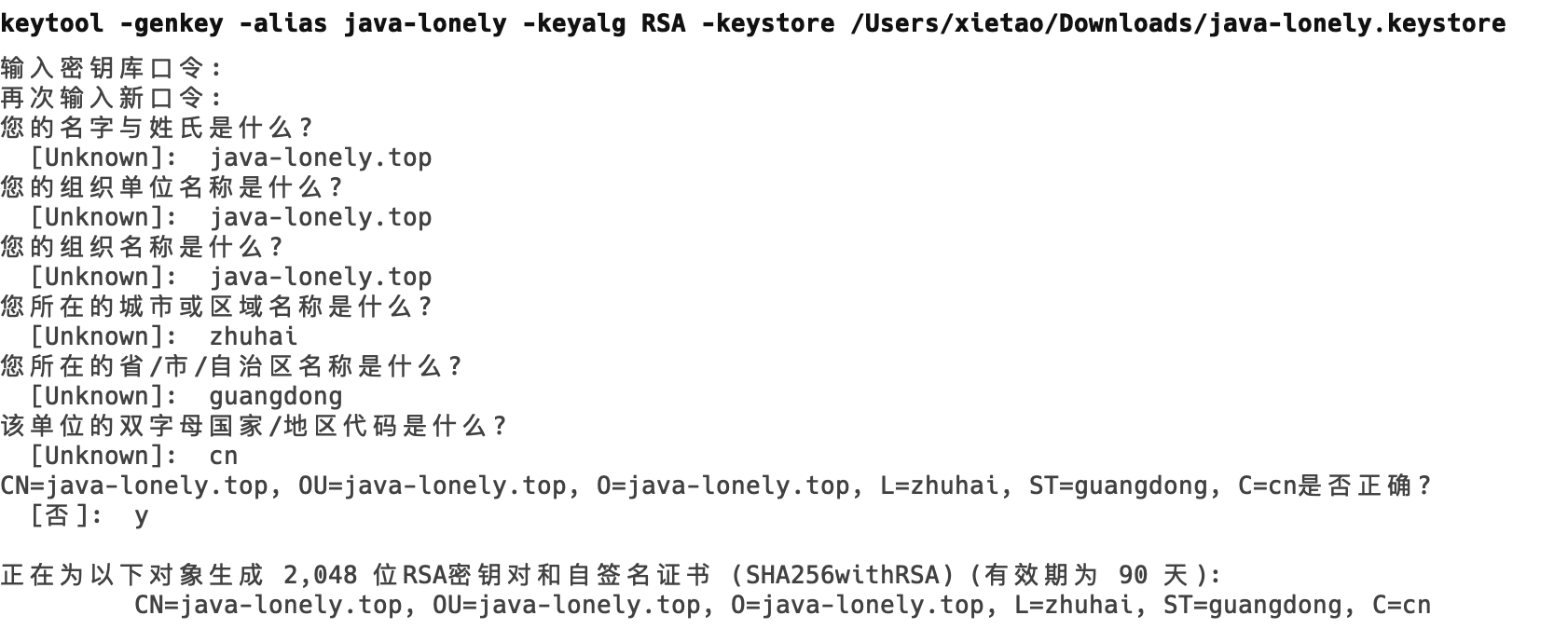 2. 从密钥库里导出证书
2. 从密钥库里导出证书
keytool -export -trustcacerts -alias java-lonely -file /Users/xietao/Downloads/java-lonely.cer -keystore /Users/xietao/Downloads/java-lonely.keystore
输入步骤1的密钥
将证书导入到jdk证书库
keytool -import -trustcacerts -alias java-lonely -file /Users/xietao/Downloads/java-lonely.cer -keystore '/Users/xietao/.sdkman/candidates/java/current/lib/security/cacerts'
此处密码为:changeit
修改tomcat的server.xml文件
<Connector port="443" protocol="org.apache.coyote.http11.Http11NioProtocol"
maxThreads="150" SSLEnabled="true" scheme="https" secure="true"
clientAuth="false" sslProtocol="TLS"
keystoreFile="/Users/xietao/Downloads/java-lonely.keystore"
keystorePass="12345678"
maxParameterCount="1000"
/> <Connector port="443" protocol="org.apache.coyote.http11.Http11NioProtocol"
maxThreads="150" SSLEnabled="true" scheme="https" secure="true"
clientAuth="false" sslProtocol="TLS"
defaultSSLHostConfigName="java-lonely.com"
maxParameterCount="1000"
>
<UpgradeProtocol className="org.apache.coyote.http2.Http2Protocol" />
<SSLHostConfig hostName="java-lonely.com">
<Certificate certificateKeystoreFile="/Users/xietao/Downloads/java-lonely.keystore"
certificateKeystorePassword="12345678" type="RSA" />
</SSLHostConfig>
</Connector>tomcat10可以参考下面的配置
下载CAS Server war包
github 官网: apereo/cas: Apereo CAS - Identity & Single Sign On for all earthlings and beyond. (github.com)
cas服务端:apereo/cas-overlay-template: Apereo CAS WAR Overlay template (github.com)
war仓库:https://repo1.maven.org/maven2/org/apereo/cas/cas-server-webapp-tomcat/
配置cas server
集成数据库
cas:
authn:
accept:
enabled: false
jdbc:
query:
- url: jdbc:mysql://localhost:3306/test?serverTimezone=GMT
user: root
password: 971023Xt
sql: select * from cas_user where username=?
fieldPassword: password
driverClass: com.mysql.cj.jdbc.Driver
password-encoder:
encoding-algorithm:
type: NONEcas server 默认帐号密码:casuser Mellon
添加依赖
implementation "org.apereo.cas:cas-server-support-jdbc-authentication:${project.'cas.version'}"
implementation "org.apereo.cas:cas-server-support-jdbc:${project.'cas.version'}"
implementation "org.apereo.cas:cas-server-support-jdbc-drivers:${project.'cas.version'}"
implementation "mysql:mysql-connector-java:${project.mysqlDriverVersion}"
表结构示例
CREATE TABLE `cas_user` (
`id` int NOT NULL AUTO_INCREMENT,
`username` varchar(30) NOT NULL,
`password` varchar(100) NOT NULL,
PRIMARY KEY (`id`)
) ENGINE=InnoDB AUTO_INCREMENT=2 DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_0900_ai_ci;开启http
在resources/services文件夹下创建一个新的JSON文件,例如web-10000001.json
{
"@class" : "org.apereo.cas.services.RegexRegisteredService",
"serviceId" : "^ (https|imaps|http)://.*",
"name" : "web",
"id" : 10000001,
"evaluationOrder" : 10
}
这里的
serviceId是一个正则表达式,用于匹配服务的URL。
在application.properties配置文件中添加以下配置:
cas.serviceRegistry.core.initFromJson=true
cas.serviceRegistry.json.location=classpath:/services
cas.tgc.secure=false客户端集成(Springboot)
添加依赖
<dependency>
<groupId>org.apereo.cas.client</groupId>
<artifactId>cas-client-support-springboot</artifactId>
<version>${java.cas.client.version}</version>
</dependency>
<dependency>
<groupId>org.springframework.security</groupId>
<artifactId>spring-security-cas</artifactId>
<version>6.1.5</version>
</dependency>添加配置
cas:
server-url-prefix: https://java-lonely.com/cas
server-login-url: https://java-lonely.com/cas/login
client-host-url: http://java-lonely.com:7777
validation-type: cas3集成security
通过 Spring Security 处理安全问题的应用程序可以利用 以自动填充 Spring Security 身份验证上下文 具有从 CAS 断言中获取为属性的角色和权限。
为此,应将 CAS 断言中的属性名称(即 )转换为 Spring Security 必须在配置中指定权限:membership
cas.attribute-authorities=membershipCAS 属性与 Spring Security 颁发机构和/或角色之间的转换可以使用以下命令进行自定义 以下 Bean 定义:
@Bean
public AuthenticationUserDetailsService<CasAssertionAuthenticationToken> springSecurityCasUserDetailsService() {
return null;
}高级配置
@SpringBootApplication
@EnableCasClient
class CasProtectedApplication implements CasClientConfigurer {
@Override
void configureValidationFilter(FilterRegistrationBean validationFilter) {
validationFilter.getInitParameters().put("millisBetweenCleanUps", "120000");
}
@Override
void configureAuthenticationFilter(FilterRegistrationBean authenticationFilter) {
authenticationFilter.getInitParameters().put("artifactParameterName", "casTicket");
authenticationFilter.getInitParameters().put("serviceParameterName", "targetService");
}
}